Top 10 powerful Hacking Tools in 2019. If hacking is performed to identify the potential threats to a computer or network then ...

Mtandao huu ni kwa ajili ya kuelimishana juu ya Kilimo na Mifugo na changamoto zake. Karibu tujifunze wote.

Top 10 powerful Hacking Tools in 2019. If hacking is performed to identify the potential threats to a computer or network then ...
Introduction Whenever security professionals recommend the 5 most important IT security practices to average users, one of the items is usua...

Reference 2019-09-25 Juniper. Masad Stealer: Exfiltrating using Telegram "Masad Clipper and Stealer" steals browser information, ...
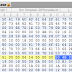
PART II Wirelurker for Windows (WinLurker) Research: Palo Alto Claud Xiao: Wirelurker for Windows Sample credit: Claud Xiao PART I Researc...